I just got off the phone with yet another scammer claiming to be from a very prominent Australian network company. I usually hang them up right away out of annoyance, but I decided to let this one continue to talk to me out of intrigue as to how his scam runs. To be honest, it made my blood boil.
This little article is to expose the scam, and for the less technical audience, to understand the actual truth behind it – as the only thing these con-artists take advantage off is our lack of understanding regarding how computers and networking works. I will not let that happen on my watch.
Let’s go step by step through the scam up to just before the point where they try to gain complete access to our computer, and see how they twist and turn very normal computer behaviour into something that looks suspicious, and induces very unnecessary panic and doubt into us.
1. The Claims
The scammers initially introduce themselves with a first name and as employees of some leading network/NBN provider. If you correct them saying you have subscribed to some other provider, they will either hang up right there, or they’ll make up some bunkum about a partnership, ownership or some other relation.
Once this is done, they’ll get to the main topic – your computer. They will tell you something you do not want to hear, but that you definitely fear: there are hackers logging into your PC and your data is at risk. If you are particularly sensitive about your data, or you have very valuable data on your system, this will pique your interest and raise questions. You will want to know for sure. You will feel like if you do not take this call seriously, you may be compromising the security of your system, and of your personal data. And this is exactly what they want, as it will allow them to frame the next few steps as concrete proof to this fallacious claim.
2. The Proof
Now the scammer will try to put themselves in a position where you see them as someone who knows their stuff, and can fix everything in your computer. Nothing scares innocent everyday computer users more than a black screen with lots of scary code on it, so this is their most common goto. “Click start and type ‘run’. And then type ‘cmd'” they’ll say. If you follow along, a black window will open up that looks something like this

In this, the scammer will spell out for you the command you have to type. “N for November, E for Echo, T for Tango, S for Sierra, T for Tango, A for Alpha, T for Tango”.
Which, if you follow correctly, will leave you with
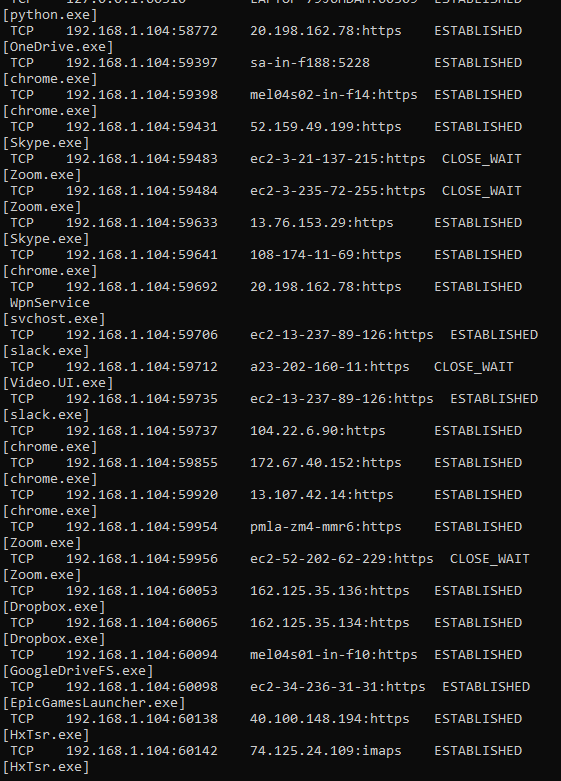
netstatI’ll get into what this command means in just a bit. Let’s examine what we see when we run it by pressing the Enter key.
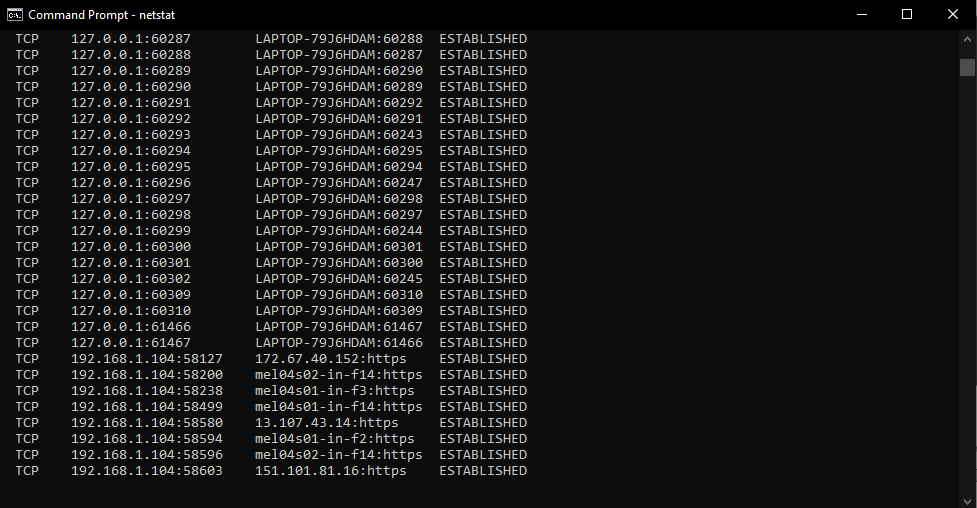
the speed and volume of the output that piles on would be enough to throw anyone off. Moreover, it will continue to slowly append more and more lines to the bottom every few seconds, as if something is continuously changing. The scammer will then ask you if you ran the command, and to describe what you see. Describing it to him will only further instil that feeling within you that this is something ominous and not right. He will also then inevitably ask you how many lines there are. When you give him an idea, he will put on a Razzie Award worthy performance of faux-shock, and tell you how dire the situation is.
He will tell you that this list before your eyes is the list of connections from hackers all around the world. Column by column, he will explain what this output means and why it spells doom for you and your data. The worst part is, most of the explanation is correct – with the tiniest change of detail in just the right place to make a very normal computer behaviour come off as scary and alarming.
He will tell you that:
- The first column is the connection type: TCP for the connections in the screenshot. This is correct
- The second column is the IP address of your computer. For the most part, and for the intents and purposes of this article, this is true.
- The third column is the IP address of all the bad hackers who are connecting to your pc. This is a load of baloney. I will explain in just a second.
- The fourth column tells you the connection status. The scammer will ask you what it says: when you say “Established” he’ll take this opportunity to provide his expert opinion that this means the hackers have established a connection to your beloved pc are are unleashing god-knows what havok inside.
The Fix
Once the scammer has you convinced, he will tell you that he can save your pc if you let him. At this point, you will likely be desperate, so you will ask him to help. He’ll have you go over and install a remote control software like TeamViewer or UltraViewer, and then he’ll most likely lock your pc and have you pay to restore it, or something else like that. Point being, you do not want to give him remote access to your PC at any cost.
Why you shouldn’t believe this
Firstly, network companies do not have access to your PC – they have no way of knowing when someone has hacked into your computer. Secondly, even if they did, they would not contact you about it without doing anything – rather they would take care of it themselves, and let you know if there were any damage done before they could take action.
The truth behind the third column
It’s time to see exactly what the third column is. Spoiler: It’s not hackers!
I will have you open your command prompt and type another command:
netstat --hBasically the same command, but this time we are going to see exactly how it works. the –h at the end is a parameter where the “h” stands for “help”. We then see the help manual for the netstat command

To translate this to English, the netstat command simply shows active network connections between your computer and the internet. It should not be alarming that your computer has so many connections – it is after all the day and age of the internet!
The long list of letters of the alphabet you see are various options (like -h) that you can send to the command to tweak or elaborate the output. We will now use the second one: -b . This will show us exactly what the third column is and put aside all doubt once and for all.
On the command prompt, type the command
netstat -bNote: you may see an error message saying it requires elevated permission. If you do, open start, type “cmd” and right-click the result and run as administrator

The output you now see will be much more telling. Can you guess what the third column is now?
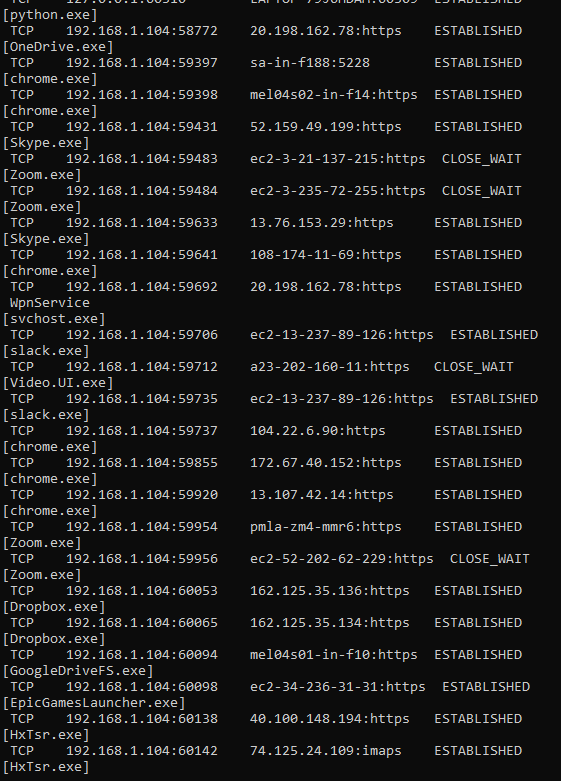
That’s right. What we thought were a bunch of hackers unleashed in our system was just the regular old network connected programs trying to do their job! This is just the list of these programs that need an internet connection in order to work. We can see Zoom, Chrome, Slack and EpicGames on mine. They keep their connections open to get notifications and updates from their respective servers.
What to do to make sure I’m actually secure
Make sure your Firewall is enabled and set. The firewall is what filters good, useful connections from reliable programs like above, from suspicious hackers and uncertified connections. You can find out more about the Windows Firewall here.
/Rant
That’s the end of my rant. Hope it helped you, and feel free to message me if you have any questions. I’ll see you guys next time!